This document is intended to guide users on how to integrate their institution’s Dell Cloud
Access Manager (DCAM) server as an SSO system to log users into the YuJa Enterprise Video
Platform. Once configured properly, a user trying to access YuJa services will first be redirected
to the IDP DCAM is setup with to login, then redirected back to YuJa where they will be verified
and logged in.
Setting up DCAM
Configuration involves creating a new application in the One Identity Cloud Access Manager console, then integrating the DCAM server on the YuJa side. Once both sides are properly configured, finalizing setup involves a test SSO using DCAM as the IDP, then activating the new SSO so that users from your institution can logged in via the DCAM system.
NOTE: For some steps, <organization> is to be replaced by the wildcard DNS of the organization associated with the Video Platform. As an example, for “https://hudson.yuja.com”, would be replaced by “hudson”.
Adding the Video Platform as an Application in the Cloud Access Manager Console
- On your DCAM server, go to: https:///CloudAccessManager/UI/Admin/Go If required to login, do so with valid credentials.
- In the Home tab, in the Applications section, click Add New.
- Click Configure Manually.
- Under Federated SSO Methods, select SAML. Click Next.
- Enter the settings manually:
Parameter Value Assertion Consumer Service URLs → Recipient https://<organization>.yuja.com/D/samlReceiveResponse Audience / SP Identity https://<organization>.yuja.com Application Logout Provide your preferred logout URL. Upload Signing Certificate YuJa does not sign nor encrypt authentication requests, so do not upload a signing certificate. Upload Encryption Certificate YuJa does not support encrypted authentication responses, so do not upload an encryption certificate. - Click Next.
- Select “Use the username (subject) provided by “Your Authenticator”. Click Next.
- Select Do not proxy this application. Click Next.
- For each of Admin and Users, select it and click Allow Role Access. Click Next.
- Enter an Application Name, for example “YuJa”. Click Next.
- Enter the following information:
a. SSO Mode - SP Initiated.
b. URL - “https://.yuja.com/D/SamlAuthentication”.
c. Section - Applications
d. Title - Description
e. Select “Add application to application portal home”.
f. Do not select “Allow users to remove application from application portal home”. Click Finish. - On the Application Created page, the Certificate is needed to configure the YuJa side. Do not download it. Simply save the text body (i.e. exclude the “-----BEGIN CERTIFICATE-----” and “-----END CERTIFICATE-----” lines, only saving the middlesection).
- In the left sidebar, under Applications, go to View and Edit. Double-click on the new application just created.
- In the left sidebar, go to Token Settings.
- For samltoken.name_id, select“urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress”. For samltoken.signature, select “AssertionOnly”. Leave all the other settings as their default values. Click Finish.
Setting up the Video Platform
- Navigate to your organization's Video Platform domain (i.e. https://.yuja.com).
- Login as an Administrator and navigate to the Admin Panel from the Main Menu. Choose the Integrations tab.
- Under Select an API to configure, choose SSO – DCAM(SAML).
- Enter the following configuration parameters:
Parameter Value IDP Login URL The IDP Login URL of your created Application. It can be found under the Federation Settings tab in the DCAM Application. Name ID Format urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress Remote Logout URL <leave this value blank> DCAM Signing Certificate Fingerprint Retrieve the certificate you obtained from the DCAM configuration. Follow the steps under How to derive the thumbprint from a certificate. Given Name Attribute The name of the attribute in the SAML Response** describing the user's given name (ie first name). - For example: urn:oid:2.5.4.42 Family Name Attribute The name of the attribute in the SAML Response** describing the user's family name (ie last name, surname). For example:urn:oid:2.5.4.4 Email Attribute The name of the attribute in the SAML Response** describing the user's emailaddress. For example:urn:mace:dir:attribute-def:mail Role Attribute The name of the attribute in the SAML Response** describing the user's role. For example: urn:mace:dir:attribute def:eduPersonScopedAffiliation IT Manager A comma separated list of values can be used -If the value received in the Role Attribute matches any of these values, the user will be provisioned as an IT manager. -For example: IT Manager Instructor A comma separated list of values can be used -If the value received in the Role Attribute matches any of these values, the user will be provisioned as an instructor. -For example: Instructor or Instructor,Teacher,TA Automatically Sync Data on User Login If checked, whenever a user logs in via ADFS their basic information will be updated based on the data received in the SAML response token. - Click Create. Click OK in the confirmation dialog popup.
- If required, you can update the configuration settings if you made a mistake. Simply click
Save to keep the changes. To test if the configuration is correct, click Test SAML Login. This should open a new tab and navigate to the IDP that your DCAM server is setup with, prompting a login. - Enter valid login credentials and login. You should be redirected back to the Video Platform, signed in as a new user.
- Once you have verified that the DCAM SSO works, you can choose to activate the
new authentication scheme for your organization.
IMPORTANT: Only activate the new authentication scheme after successfully performing a test
login and are ready to make it available for all users in your institution.
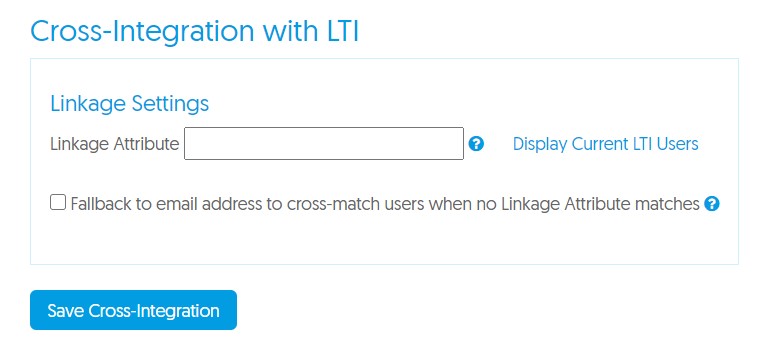
Cross Integration with LTI
If your institution has enabled both LMS Integration via LTI and also SSO access, then you have the choice to link the two integrations. We generally recommend this because it means that irrespective of whether your users log in via their LMS or their SSO, they will be presented with the same Video Platform account information. In contrast, if Cross Integration with LTI is not set up, a user who uses both their LMS and SSO with YuJa will be provisioned with two separate accounts, which in many cases isn’t ideal.
- Configure your LMS to pass a custom LTI parameter to the YuJa tool called
lis_person_sourcedid which contains the cross-matching SSO value. This can be an email,
employee ID, or other field. You may need to consult your LMS platform’s product
documentation on how to set custom LTI parameters. The Video Platform will make use of this feature to link the two login methods to the same account. - Obtain the specific attribute name used in the SAML Response token whose value
corresponds to the unique identifier used by the LTI provider.
a. For example, if the unique identifier is the user's email address, then the linkage
attribute might be “urn:mace:dir:attribute-def:mail”
b. A complete list of the possible attribute names can be found in the DCAM metadata
file, in the Attribute tags. - Enter this value into the Linkage Attribute field. Note: This textbox will only appear if your
institution has enabled LTI access. - Click Save.
How to Derive the Fingerprint of a Certificate
The fingerprint of the IDP’s certificate is used for additional security purposes when the SP is verifying a SAML response from the IDP. To derive the certificate’s fingerprint, follow the instructions below:
- In the ADFS IDP metadata, extract the X509 certificate. This should be located under:
<IDPSSODescriptor>--<KeyDescriptor use="signing">--<KeyInfo>--<X509Data>--<X509Certificate> - Once you have the certificate, go to the following website: https://www.samltool.com/fingerprint.php
- Paste the certificate in the X509 cert textbox.
- Make sure sha1 is selected as the Algorithm.
- Click Calculate Fingerprint.
- Copy the Fingerprint value generated. This is the value used in the database. Note: The fingerprint should be an array of 20 bytes for sha1.